Strong ISMS - the foundation of great infosec
Do you have a complete overview of your body of controls?
Have you mapped them across various frameworks and legislations to avoid double work?
Are you capable of reporting status to auditors and management?
Wired Relations is every tool information security teams need to build a great ISMS (Information Security Management System). Build on a standardised structure, you get an eagle-eyed overview and reclaim full control.

Here’s a breakdown of the benefits of
Wired Relations…
Work with multiple regulations and frameworks
Do controls with recurring tasks and evaluation
Mapping across frameworks
Companies all over Europe already build sustainable GRC programmes with Wired Relations




























Infosec frameworks: An overview of the most common ones
What an ISMS solution should do
You need a complete overview of your body of controls within the frameworks and regulations relevant to your organisation. Also, you need to map them, so that you know what controls are in more than one of the frameworks. Lastly, you must know when to do the control and how to report to internal auditors and management.
That’s what Wired Relations does and it gives you what you need to make sound decisions and distribute resources efficiently.
Load pre-build frameworks
Load all controls from popular frameworks in no time. Frameworks like ISO 27000-series, NIS2, NCIS, ISAE3000 and more.
.webp)
Customise control sets or build your own
Not all standard framework controls fit your needs, so you can of course customise them as you want, remove them completely, or build a new set.
.webp)
Do one control, check it off in every framework
When you finish a control task, you can cross it off, not just in one framework, but in all frameworks that include the same control. The governance model works across all frameworks to reduce your workload.
.webp)
Key functionalities of Wired Relations
A selection of the key features that will elevate your Governance programme.
Load the controls from ISO 27001 (and 27701) with one click and map them across other regulations and frameworks.
We’ve mapped the requirements in NIS2. Upload them with one click, manage them and map across other frameworks.
Load the controls from CIS 18 with one click and map them across other regulations and frameworks.
Manage and map multiple frameworks from one place. ISO 27001 / 27002 / 27701, NIS2, ISAE3000, CIS18, NIST, SOC 2.
Manage security incidents intuitively and get the insights needed to prevent them in the future.
The structured approach to risk management makes it possible to get an overview of all your risks and manage them proactively.
Say goodbye to the manual labour of doing vendor audits. Get back control and overview.
Reporting on risks, information security status, security incidents and more becomes easy with all data in one solution.
Central storage of your documents - access from anywhere. Never again lose important information.
Get a complete and connected overview of all your systems and vendors to secure robust security.
Implement any framework or control set into Wired Relations and make it fit your business and operation.
Get a full overview of your workload with upcoming and recurring tasks. Manage your resources by looking into your yearly workload view and schedule tasks for when there is time.
Managing all your controls
With Wired Relations, you get a rock-solid approach to manage all controls of your ISMS, ISO, NIS2 and other frameworks. Get a clear view of how far you are, what you are missing and who is responsible.

Load pre-build frameworks like ISO
Load all controls from popular frameworks in no time. Frameworks like ISO 27000-series, NIS 2, NCIS, ISAE3000 and more.
Customise control sets or build your own
Not all standard framework controls fit your needs, so you can of course customise them as you want, remove them completely or build a new set.
In-app guidance for each control
The pre-built controls come with legal help text, examples of information and more to help you fill it out and prevent under or over-implementation.
Rule your day-to-day security operations
Get a set of power tools built for data protection operations. Work smoother than ever, waste less time on admin work and always know your next task.


Control execution
See how you should execute specific controls, directly linked with tasks and owners.

Task overview
Get both KanBan and list overviews for your tasks to work in the right view.

Recurring controls
Build a yearly task cycle with recurring tasks of controls, assessments, audits and more.

Task types
Label tasks, filter by type and customise labels for your own needs.

Task evaluation
Finish tasks and evaluate them with smilies and follow-up notes, so you know where your gaps are.
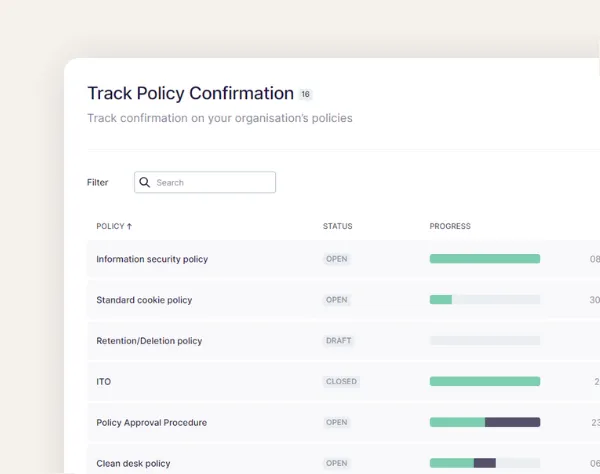
Policy adoption
See all your policies from one view and easily see what policies that needs better adoption.
Choose the right controls based on risk
Do thorough risk assessments to find the threats and weaknesses in your programme and choose the right mitigations and controls to strengthen security.
Take a threat-based approach to risk management.
Colored risk matrix for each overview.
Connect to security measures.
Use standardised risk caltalogue for easy reporting.
See both calculated and residual risk.
See all connected tasks to each risk assessment.


Get buy-in from management with overview and reporting
Everything starts by understanding the risk landscape and how effective your mitigations and controls are in lowering risk. Being strategically involved means good reporting. But a good report also gives you the overview and status you need to know where to prioritise.

Get the full picture of your security incidents.
Understand which systems and departments face the biggest risks.
Asses your SoA to get status on control efficiency.
Prioritize what needs your attention and use it for management reporting.
Easily plan your implementation of tasks to be done.
Present your reports to management and get approval without hassle.
Power features
Segmented Governance Doc
Make a printable governance document and tailor it to the segment to whom you are presenting.
Automated SoA
Generate a SoA document for reporting at any given time. Just click generate and you have a status.
1-click load of frameworks
Load frameworks like ISO 27002, NIS 2, NIST, CIS 18 and more, with prefilled controls.
Task re-distribution
When a co-worker stops, you can redistribute all tasks to new owners before deleting the user. No more orphan tasks.
Policy adoption overview
Get a clear cut view of how many have adopted policies and easily resend to those who need reminding. Never again have someone say: “I never saw that policy.”
Workload dashboard
Do you make good use of your limited resources? The Workload Dashboard gives you that insight.
Recurring controls
Information security is an ongoing process. Make controls recurring from weekly to 3-year intervals to ensure you never forget anything
Task evaluation
Evaluate completed tasks with emojis and follow-up notes to have your colleagues report back to you and see what finished tasks you need to return to.
Framework link
Link controls across frameworks. Done in one framework, means easy check-off in the next. That heavily reduces double work.
ISO implementation guide
Load all ISO 27002 controls with advice on implementation built into each control - right where you need it to reduce administrative work and mistakes.
Workflow connection
Get seamless connections between assessments, systems, vendors, processing activities and tasks.
Custom controls
Implement any framework or control set into Wired Relations and make it fit your business and operation.
The full Wired Relations GRC solution
Our GRC solution features unique modules that work seamlessly together. They can also be combined to fit your specific governance, risk, and compliance needs
GRC solution
Compliance
Risk
Ready to experience Wired Relations - book your demo here
A smooth onboarding and continued customer success
We recognise the importance of a seamless start with our solution. Thanks to Wired Relations' intuitive design and ready-to-use approach, our onboarding process is straightforward and structured, unfolding in four phases over the course of four weeks.

Connect your essential tools with Wired Relations
Integrating your key applications with a GRC solution is vital for saving time, streamlining workflows, and improving both user management and data quality in your compliance efforts.
With Wired Relations, you can connect your line-of-business systems to automate repetitive tasks, reduce manual data entry, and boost data accuracy—ultimately driving productivity and operational efficiency. Additionally, our integrations for user and group provisioning, as well as Single Sign-On (SSO), make access control easier and more secure.
We offer pre-built integrations and Public API.
.webp)
Security and data
The security of our users’ data is a fundamental aspect of every step in the development process at Wired Relations – it is embedded in our DNA.
We respect your privacy and ensure that your data is kept safe. Our solution's security is state-of-the-art and continuously updated to meet the latest requirements, both those we set ourselves and those dictated by industry standards.
We are committed to openly and transparently disclosing our data handling and management practices.
.webp)
Being compliant is not the end. It’s the beginning
Governance, Risk & Compliance is a process, not a project. Constantly keeping structure, overview and control is what turns fragile privacy and information security into sustainable GRC programmes.





.jpg)
